This is a common root cause of many business problems like a go-to-market that can’t get off the ground. Signs are there if your teams frustrated with each other. Better positioning for Tech B2B will help.
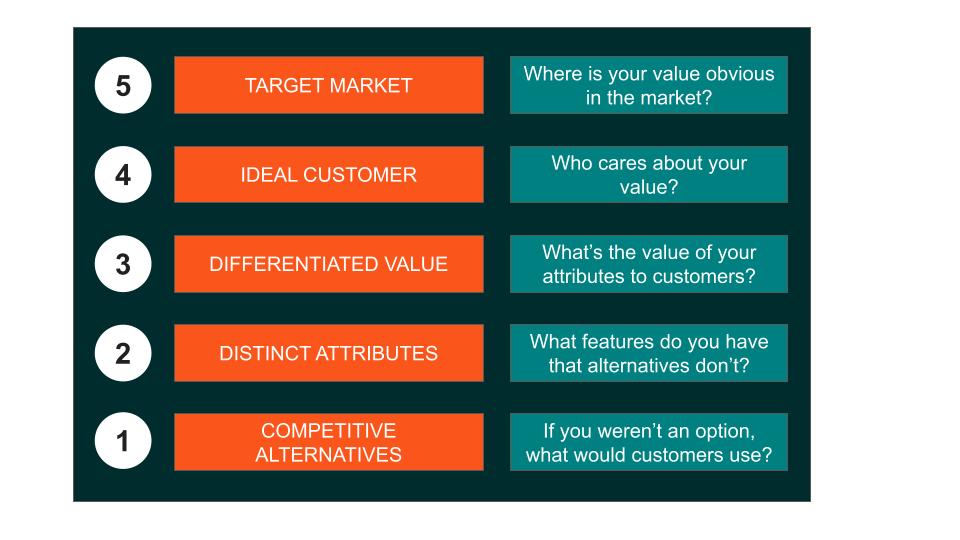
This guide shows a simple 5-step process you can do with your team. Positioning isn’t just marketing’s job: it’s everyone’s job, and needs to be sponsored by the biggest boss you can find — the CEO!
This guide is aimed at a team, led by the CEO, who are tasked with creating an agreeable positioning statement that is the foundation of a unified go-to-management approach.
Inspired by the years of work I spent doing marketing and presales at VMware, Cisco, VCE and the books Challenger Sale and Challenger Customer. Special mention goes to the fabulous Queen of B2B Positioning, the inimitable April Dunford.
Example 1: Tech Vendor
Has an MVP for a new “Data Security Posture Management” solution.
Example 2: Security Partner
Security experts seek to scale their professional services to more clients.
Step 1 - Competitive Alternatives
Imagine for a moment, “What if we weren’t even an option? Where would our prospects look? What would our customers buy instead?”
Some find it weird that positioning starts with nothing really to do with you. It starts outside of your company. It focuses on your prospects, your customers, and your competitors.
This makes perfect sense and explains why positioning is not messaging. Messaging comes after positioning.
Messaging is where you get to align yourself with prospects, customers, partners, and competitors. But before you do that, you need to see things from their point of view.
This is Step 1 of positioning: taking outside-in perspective. Time to let go of the ego and send the narcissist away! 😅
One of the first surprises of of looking at alternatives is that it’s not just your competitors that are in scope. It’s not “that other vendor” or “that other service provider” — the first two things you need to consider are the prospects own inertia, or their propensity to “do it themselves”.
The Continuum of Competitive Alternatives
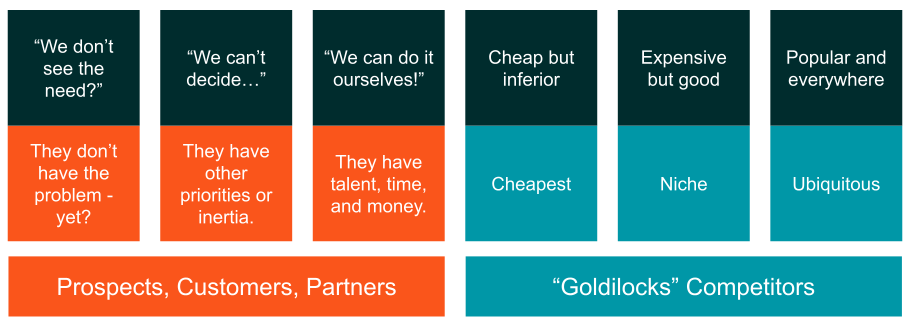
We’re going to ignore the lobster-coloured left-side of the continuum because that’s better handled in the Challenger Customer material.
Let’s, instead, focus on the teal-coloured right-side of the continuum as we test our examples.
What would a prospect do if you didn’t exist?
Tech Vendor Competitive Alternatives
What other vendors offer a similar product?
While there are ten options on the market, they fall into three categories.
The cheap options are mediocre at everything, but they promise a “get started quick and cheap” option.
The niche option is very strong in the key area, but doesn’t even bother in other areas.
And the ubiquitous option is part of a large suite where the buying decision is made by procurement based on discounts and scale, not product capability.
Security Partner Competitive Alternatives
Where else do customers find these security services?
If customers need the outcomes that the security partner provides through professional services, the only alternatives available are:
a) Vendor professional services — which are expensive and hard to get.
b) Reseller/partners that have “shallow skills” at best.
c) Last option is boutique or consultant companies who have limited bandwidth and can only be found through referrals/word of mouth.
Step 2 - Distinct Attributes
What features do you have that alternatives don’t have?
Features don’t have to be just product widgets, capabilities, or service deliverables. They can also include domain expertise (e.g. FinTech, Retail), geographic locality, and certifications, bandwidth, scale and much more.
In this case. by comparing the competitive alternatives to each example, we can spot at least one distinct attribute.
Tech Vendor Distinct Attributes
What does your product have that the others don’t have?
As our product has been recently developed, it focused on today’s new challenges rather than yesterday’s legacy problems.
This means that customers who only have legacy concerns might not be prospects and will probably qualify out.
The new feature is focused on the new PCI global payment standard so customers are going to have to upgraded at some time. But new companies, of which there are many, can use our modern capabilities from the start.
Security Partner Distinct Attributes
What’s different about your security service?
Our service is a combination of GRC, data security specialization, cloud technology, and is focused on an industry compelling event where customers of a large ERP platform need to migrate in the next few years.
Other services companies only do “one leaf of branch of the tree”, whereas we do the complete solution so we can focus on an outcome 100% aligned to what customers *must* do.
Step 3 - Differentiated Value
What’s the value of your distinct attribute(s) to your customers?
Imagine you’ve just explained to a prospect what you think is different about you compared to the competitive alternatives.
What would they say?
We’re looking for more than polite interest. We’re looking for enough value that they will persuade their colleagues to agree to pay money and invest time in your solution.
The pain of same must be more than the pain of change.
Tech Vendor Differentiated Value
Does your customer attach enough value to your distinct attribute(s)?
The customers that do see the value to them say that it’s going to speed up and de-risk their alignment with the new standard. The alternatives aren’t palatable as they are either “stitch something together ourselves’ or wait for the incumbent vendors to get their act together.
Security Partner Differentiated Value
What’s the value of your security service?
The larger, distributed customers with production systems say that the service is very helpful because it reduces the unavoidable work required into neat work packages where, proven once, it should be reliable across other locations.
Step 4 - Ideal Customer
Who cares about your value?
Based on the customers that saw value, is there any commonality in them? If you spoke with more customers of the same “type”, would it be a similar conversation?
Tech Vendor Ideal Customer
Imagine this is a testimonial: who is it? What do they say?
A similar conversation is likely if the customer is:
a) present in multiple geographies;
b) payments and compliance with PCI-DSS are core to their business;
c) their current system needs to be upgrade to comply with the new standard;
d) and they have some adjacent needs that they can solve in the same change.
Security Partner Ideal Customer
Imagine this is a testimonial: who is it? What do they say?
It looks like mid-size ERP and CRM customers have a similar challenge that these solution addresses.
Some them will have long-term agreements with other vendors or solution providers/systems integrators/outsourcers that might be a barrier to entry: or an opportunity to unseat the incumbent!
Step 5 - Target Market
Where is your value obvious in the market?
Now that we know our competitors, our difference, our value, and have an ideal customer: how many of them are they, and where are they?
Tech Vendor Target Market
Can you identify company types, verticals, compelling events or other market identifiers?
Research shows that the main regions are north america, UK, EMEA, and MENA.
In those regions, we’ve found that there are 10,000 customers of the right size, using competitor tech, and *might* need to move to the new standard.
We think it would be good to focus on one market first, and pick a subset of the total addressable market and test the positioning more and try to find early wins.
Security Partner Target Market
Can you identify company types, verticals, compelling events or other market identifiers?
We can only operate in the US, and if we focus on enterprises of the right size, a discussion with one of our tech vendors that are part of the solution tells us that we might expect 10% of the total addressable market.
However, we’ve been told that one of the large USA distributors would like to partner with us because they see it’s a gap in the market and they’d like to resell and licence the IP.
Next steps
Once you’ve completed your internal positioning, what do you do next?
Write it up. Test it internally. Test it externally. Try to get to a stable version…. then…
Lock your internal positioning. Do not change it. Set it in stone.
Then move onto messaging and all the other go-to-market activities you’ve got to do.
But don’t change the positioning when you find things that don’t fit. Make a note of them.
Only revisit your internal positioning in something like six months time, as part of a well-managed process.
Resources
- Team brief
- Worksheet
- Workshop
- Report
Other Viewyonder Guides
Internal Positioning
5-step guide to creating your own internal positioning, an essential foundation for your go-to-market.
Blog Post
4-step guide to creating a < 1200 word blog post, from idea and brief, to final, atomization, and distribution.
Competitive Intelligence
Move from lo-fi best effort to professional and performant competitive intelligence.